Persistent XSS vulnerability in IsarFlow
Web-based dashboards are the centerpiece of many enterprise applications. They bundle information, facilitate control and enable efficient collaboration. In a recent audit of the software IsarFlow up to and including version 5.23, we identified a critical security vulnerability: malicious code could be permanently injected into the dashboard title, which was automatically executed when certain dialogs were called up.
The functionalities relating to the “user dashboard” in particular posed an increased risk: administrators who manage various dashboards in this view ran the risk of an attacker executing malicious code with extended permissions via manipulated dashboard titles. This affected sensitive actions such as deleting or editing dashboards.
Following our notification, IsarNet Software Solutions GmbH reacted quickly and fixed the issue with versions 5.25.14 and 5.26.4.
Learn more in the following article about how attackers exploit such vulnerabilities and what measures you can take to protect your company against comparable risks. We are happy to assist you as a partner for professional security analyses and sustainable protection concepts!
A persistent Cross-Site-Scripting vulnerability was found in the IsarFlow version 5.23 (or earlier) software of IsarNet Software Solutions GmbH. We reported this vulnerability to the software manufacturer, who immediately fixed the problem and closed the vulnerability in versions 5.25.14 and 5.26.4.
Description
The title of the dashboard is not correctly encoded in all places and is vulnerable to persistent Cross-Site Scripting.
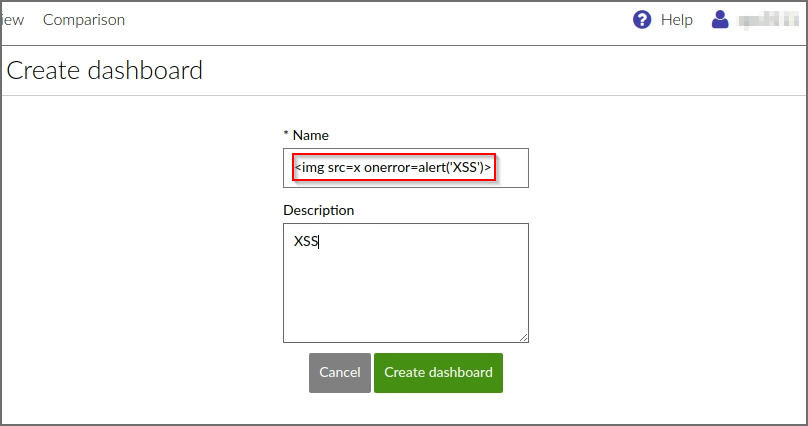
When the "Delete Dashboard" dialog box is opened, the JavaScript code is executed.
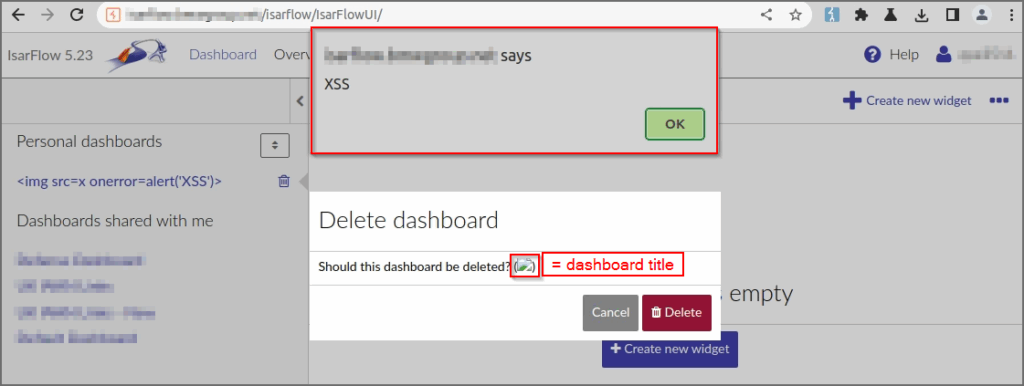
In addition, the "User Dashboard" menu offers an administrator the option of searching and editing all dashboards created by users. The title of the dashboard is also not encrypted in this view, which leads to the execution of the payload and can therefore be used to attack user accounts with higher permissions.
Affected component: IsarFlow Portal
Attack type: Remote
Impact Code Execution: True
Attack vectors: To exploit the vulnerability, an attacker needs access to the application.
Reference: TBA
Discoverer: Max Maier (mgm security partners), Benedikt Haußner (mgm security partners)